Cybersecurity & Compliance
Already SOC 2 Certified? Here's Your Strategic Path to HITRUST Certification
For any organization handling sensitive data, achieving SOC 2 compliance is a significant milestone. It demonstrates a foundational commitment to security, availability, and confidentiality, building critical trust with your customers. But for companies in the healthtech space or those serving enterprise clients with stringent security requirements, a new question often arises: What’s next?
The answer is frequently HITRUST certification.
While SOC 2 is an excellent framework, HITRUST is the gold standard, particularly for handling Protected Health Information (PHI). If you're a healthtech company or a SaaS provider looking to move upmarket, HITRUST isn't just an option; it's a competitive necessity.
The good news? Your hard work achieving SOC 2 compliance gives you a massive head start.
Why Bother with HITRUST if You Already Have SOC 2?
Think of it as building on a strong foundation. SOC 2 proves you have good security principles. HITRUST proves you have implemented a rigorous, prescriptive, and certifiable control set that is specifically designed to meet the complex regulatory requirements of the healthcare industry, including HIPAA.
- Unlock Enterprise & Healthcare Deals: Many large healthcare organizations and enterprise clients will not even consider a vendor without HITRUST certification.
- Streamline Security Questionnaires: A HITRUST certification can drastically reduce the time spent answering complex security questionnaires from potential customers.
- Build Unbreakable Trust: It is the single most effective way to demonstrate your commitment to protecting sensitive data.
The Overlap: How Your SOC 2 Work Accelerates HITRUST
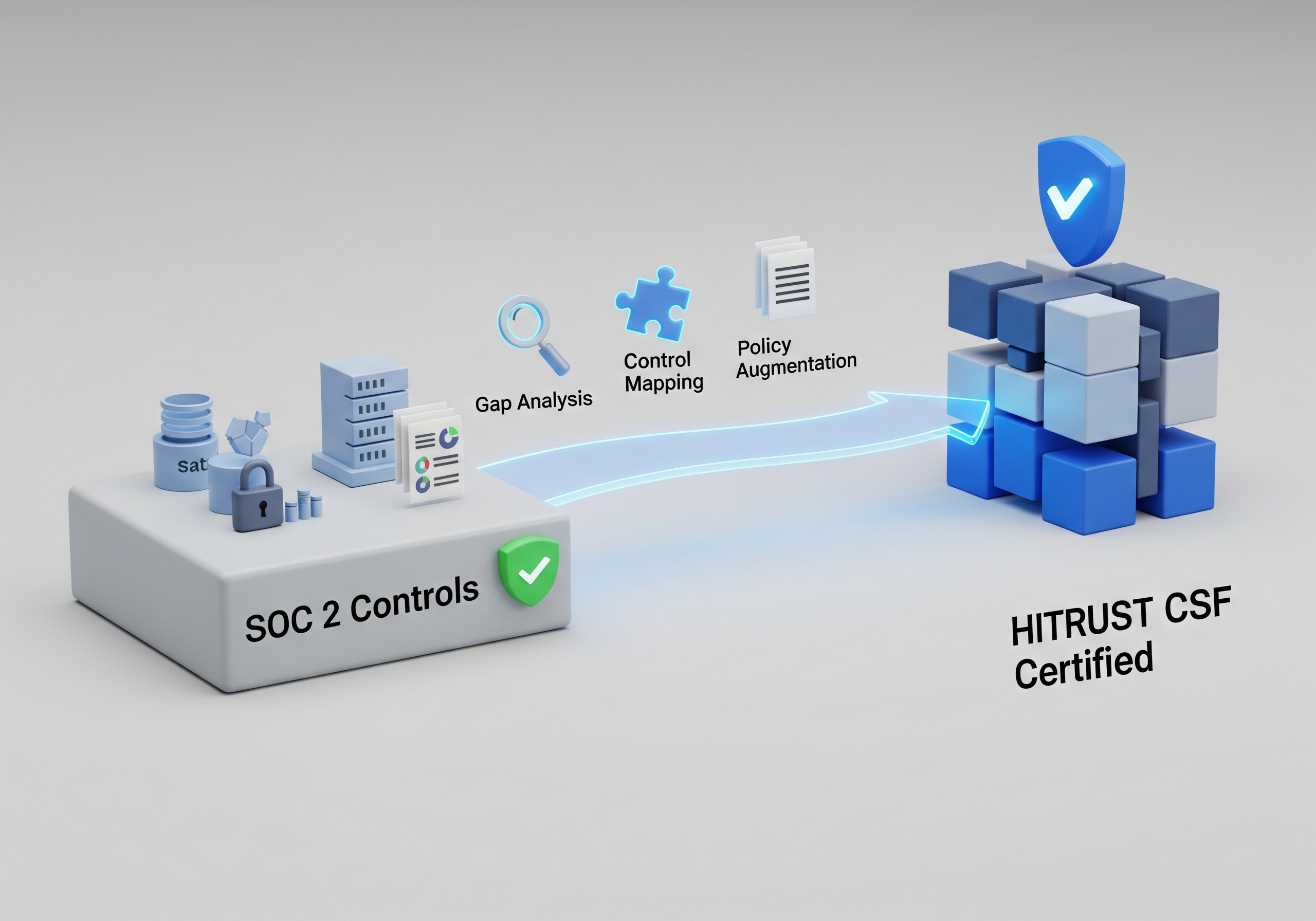
The HITRUST Common Security Framework (CSF) is designed to be comprehensive. It actually incorporates the SOC 2 Trust Services Criteria. This means a significant number of the controls you implemented for your SOC 2 audit are directly applicable to your HITRUST assessment.
Your existing documentation, policies, and procedures for things like access control, change management, and risk assessment don't need to be reinvented; they need to be mapped and, in some cases, augmented to meet HITRUST's more prescriptive requirements.
Your 4-Step Path from SOC 2 to HITRUST
Leveraging your SOC 2 certification is the key to an efficient HITRUST process. Here’s the strategic path ahead:
Step 1: Scope Definition & Gap Analysis
The first step is to understand the difference. We start by mapping your existing SOC 2 controls against the HITRUST CSF. This isn't just a checklist exercise; it's a strategic analysis to identify the specific gaps between your current state and what HITRUST requires. We identify which of your existing controls can be directly inherited and which need enhancement.
Step 2: Policy & Procedure Augmentation
HITRUST is more prescriptive than SOC 2. Where SOC 2 allows for flexibility in how you meet a control, HITRUST often has very specific requirements. This step involves updating your existing policies and procedures to meet these more rigorous standards. This could involve enhancing your risk management program, refining your incident response plan, or strengthening your third-party vendor management process.
Step 3: Evidence Collection & Control Implementation
With the roadmap from the gap analysis, we work with your team to implement any new required controls and gather the specific evidence HITRUST assessors will look for. Because you've already been through the evidence collection process for SOC 2, your team is already familiar with the discipline required, making this phase much smoother.
Step 4: Assessment & Certification Management
Finally, we manage the formal assessment process with an authorized HITRUST External Assessor. We act as your liaison, ensuring all documentation is correctly prepared and submitted, and guiding your team through the assessment to a successful certification.
Don't Start from Scratch. Build on Your Success.
Achieving SOC 2 was a major accomplishment. Now, you can leverage that investment to reach the next level of security assurance. The path to HITRUST is a clear, manageable process when you have a partner who understands how to map your existing controls and bridge the gaps efficiently.
